-
Content Count
8 -
Joined
-
Last visited
Posts posted by AdvisorBM
-
-
Information security basics for company + checklist for checking information security of organizations.
 In this article, I would like to talk about information that needs to be protected from attackers planning to harm your business. Please note that we will not be talking about the technical part of companies' operations, but about social engineering aimed at the vulnerabilities of your employees.
In this article, I would like to talk about information that needs to be protected from attackers planning to harm your business. Please note that we will not be talking about the technical part of companies' operations, but about social engineering aimed at the vulnerabilities of your employees.We added a free for public use "CHECKLIST FOR CHECKING THE INFORMATION SECURITY OF ORGANIZATIONS". We hope that this checklist and the information in this article will add peace of mind and information security to your organization.
You can read the checklist at the end of the article.Email
 More often than not, email is the main entry point into the secrets of your company and its personal staff. Every official company website contains contact information that includes an email address with the company domain. For example, info@nameoforganization.com or hr@nameoforganization.com.
More often than not, email is the main entry point into the secrets of your company and its personal staff. Every official company website contains contact information that includes an email address with the company domain. For example, info@nameoforganization.com or hr@nameoforganization.com.This is consistent with business ethics, but in today's Internet there are a huge number of tools (e.g. Google Dorks, phonebook.cz, hunter.io etc) that, using the domain, collect other addresses that the organization may not have wanted to publish to the general public. This might reveal something like ciso@nameoforganization.com, andreypetrov@nameoforganization.com, SolyuVseSekretyKontory@nameoforganization.com.
The mere presence of a work e-mail not only gives the opportunity to establish direct contact with the employee bypassing the public relations department, but also allows colleagues to misuse it, namely to register accounts in social networks, order deliveries and so on, so on, so on. All of this subsequently gets ducked. With such email addresses, we can find a lot of interesting personal information that is useful for hackers and cyber blackmailers.
Employee photos on the company website
 Yes, photos on a company's website can help find your employees' social media accounts. In most cases, this information has no commercial value, but it is a great opportunity to gather information about an employee's private life, which can result in such a well-built social engineering campaign that the attacker will not even notice the catch.By the way, there are quite a few tools for searching social media accounts by face. For example, FindClone, SearchForFace, and even simple google.pictures.Public activity
Yes, photos on a company's website can help find your employees' social media accounts. In most cases, this information has no commercial value, but it is a great opportunity to gather information about an employee's private life, which can result in such a well-built social engineering campaign that the attacker will not even notice the catch.By the way, there are quite a few tools for searching social media accounts by face. For example, FindClone, SearchForFace, and even simple google.pictures.Public activityIn reality, photos and public activity are not as critical vulnerabilities as personal data that can be gleaned from email addresses. To exclude a company's public activity is to cut off 80% of marketing. Some things are worth publicizing and some are not.
An example of a social engineering attack would be a text like this: "Good afternoon, I saw you at the conference "Legends of SOC - 2023". We liked your presentation very much. We would like to propose cooperation. Terms and conditions and a detailed offer are in the attachment". Agree, tempting! Especially if your company slightly underpays a sysadmin, and he is in search of a more favorable offer. There is a high probability that even an experienced IT specialist will first open the attachment and only then think about it.
Files on the company website
 You may think that you have hidden all the unnecessary files, but Google search robots have indexed everything carefully. It is very easy to check this. For example, your website is: rogaikopyta.site. Type in the search bar google: filetype: (here without a space file format -- pdf, doc, docx, xls, txt) site:rogaikopyta.site. Next, we check that nothing unnecessary is suddenly not in the public domain.
You may think that you have hidden all the unnecessary files, but Google search robots have indexed everything carefully. It is very easy to check this. For example, your website is: rogaikopyta.site. Type in the search bar google: filetype: (here without a space file format -- pdf, doc, docx, xls, txt) site:rogaikopyta.site. Next, we check that nothing unnecessary is suddenly not in the public domain.There are a number of documents that a legal entity cannot not publish, but what is not included in this list, it is better to clean, because unnecessary information about your employees, counterparties, financial assets - all this is excellent food for a potential attack.
We also want to pay attention to which employees pose the greatest threat to the information security of companies.
 Most information security studies indicate that the weakest link in security measures is the employees, as they are the ones who have full access to all the resources and documents of the organizations.New IT employeeA new IT employee can inadvertently cause huge damage to a company's security. Today, hackers are using more and more sophisticated methods to infiltrate internal company resources, such as social engineering. A newly hired IT employee is unfamiliar with the protocols and processes responsible for the secure transfer of files over a network, and is therefore an extremely attractive target for cybercriminals looking to gain full access to corporate information.
Most information security studies indicate that the weakest link in security measures is the employees, as they are the ones who have full access to all the resources and documents of the organizations.New IT employeeA new IT employee can inadvertently cause huge damage to a company's security. Today, hackers are using more and more sophisticated methods to infiltrate internal company resources, such as social engineering. A newly hired IT employee is unfamiliar with the protocols and processes responsible for the secure transfer of files over a network, and is therefore an extremely attractive target for cybercriminals looking to gain full access to corporate information.System administrator
In many companies, system administrators handle the main information security issues. A sysadmin doesn't just handle the technical aspects, but has a huge responsibility for the tangible and intangible assets and reputation of the organization. Moreover, he knows almost everything about the company, has access to all confidential data, so under certain circumstances he can be subjected to pressure from cybercriminals.Top management
Rather oddly, a company's CEO is actually often a huge threat to the company's information security. According to the Ponemon Institute, more than half of the leaks involving employees are caused by top management. Such losses are clear proof that hackers see not only middle managers but also top management as their targets. Executive assistants are also the carriers of very valuable corporate information. They have access to all credentials, passwords, financial reports and internal documentation. This is what makes them a particularly attractive target for hackers.Security Consultant
If your organization needs a complex, multi-stage security system, be prepared to partner with a variety of service providers from this field. Remember, however, that an external security consultant brought in to determine the current level of security and set goals for the organization's IS direction has full access to all internal company resources and sensitive data, which hackers are well aware of.External vendor
Large companies often utilize multiple external vendors at once. Daily hacker attacks confirm that once vendors gain access to a company's internal systems and networks, those systems and networks are particularly vulnerable to cyber threats. To protect themselves, companies must give vendors limited, controlled access.Fired employee
A fatal mistake many companies make is neglecting to close access to internal resources and networks to former employees. By making this mistake, organizations become even more susceptible to cyberattacks. The only true solution is to immediately delete all accounts of employees who are no longer with the company. Moreover, former employees can easily take databases of potential and current customers and other confidential information with them and put it freely available online.Temporary employee
Temporary employment is a very common phenomenon, especially in the service and sales industry. The IT sector is no exception, as very often employees are needed here on a temporary basis to help close some tasks. These employees are given access to various corporate portals and systems where the company's most important information and data is stored. Moreover, temporary employees are given the use of corporate laptops, tablets and smartphones. This is why these employees should be considered full-fledged in the organization and protected from information security threats. I would like to finish this article with a quote from Bruce Schneier: "In terms of security, the mathematical apparatus is flawless, computers are vulnerable, networks are lousy, and people are disgusting."Remember that it is employees and their negligence towards security measures that pose a huge threat to a company's IT security.
ADDITIONAL INFORMATION THAT MAY HELP YOU.
-
BLOCKCHAIN REVIEWERS:
UNIVERSAL REVIEWERS:
VISUALIZATION OF CRYPTOCURRENCY TRANSACTIONS:
CRYPTO WALLET IDENTIFICATION:
REVIEWS OF CRYPTO WALLETS:
ADVANCED QUERY OPERATORS IN GOOGLE:
BLOCK ANALYSIS:
CRYPTOCURRENCY STORAGE FILE TYPES:
- Armory: %appdata%\Armory (.wallet)Bitcoin
- Unlimited/Classic/XT/Core: %appdata%\Bitcoin
- (wallet.dat)Bither: ‘%appdata%\Bither’ (address.db)Blockchain:
- (wallet.aes.json)MultiBit HD: %appdata%\MultiBitHD
- (mbhd.wallet.aes)Electrum:
- %appdata%\Electrum\walletsmSIGNA:
- %homedrive%%homepath% (.vault)
OTHER USEFUL PROGRAMS FOR INVESTIGATIONS AND OSINT IN BLOCKCHAIN:
OTHER TOOLS AND INFORMATION:
-
Original text and other information on OSINT is available at>>>>
 His nostrils were permanently flared, as though he sniffed invisible winds of art and commerce. William Gibson, "Count Zero"
His nostrils were permanently flared, as though he sniffed invisible winds of art and commerce. William Gibson, "Count Zero"In this article I will show:
How, using the basics of financial investigation and OSINT, we can prove the affiliation of cryptocurrency addressesHow by analyzing the transactions of two or more ETH addresses, we can aggregate them into a cluster (i.e. multiple addresses controlled by the same entity)How the attacker's economic activity dataset changes once the addresses are clustered togetherLet's get started!
The most popular onchain detective ZachXBT once posted the following tweet For those unfamiliar with English, let me explain. Using a phishing site, a hacker gained access to the victim's address and stole 3 ERC-721 tokens (NFT). Immediately after the theft (i.e. after sending the tokens from the victim's address to his address, 0x864875aef79B107221bEE89C8ff393BD2B666d96) the hacker sold the NFT on the marketplace Opensea.io. The criminal profits were then laundered through the Tornado.Cash mixer.While our hands are itching to get the target address into https://etherscan.io sooner rather than later, we'll stop on the shore and turn to the theory. The criminal first stole and then sold tokens that use the Ethereum blockchain infrastructure.
For those unfamiliar with English, let me explain. Using a phishing site, a hacker gained access to the victim's address and stole 3 ERC-721 tokens (NFT). Immediately after the theft (i.e. after sending the tokens from the victim's address to his address, 0x864875aef79B107221bEE89C8ff393BD2B666d96) the hacker sold the NFT on the marketplace Opensea.io. The criminal profits were then laundered through the Tornado.Cash mixer.While our hands are itching to get the target address into https://etherscan.io sooner rather than later, we'll stop on the shore and turn to the theory. The criminal first stole and then sold tokens that use the Ethereum blockchain infrastructure.In order to operate the tokens, you need some amount of cryptocurrency to pay transaction fees. In our case it is the Ethereum blockchain, which means you need some ETH to send tokens or sell them.
Let's try to find out where the hacker's address 0x8648... ETH he needed to pay commissions came from.
This line of enquiry is called a source search
Open Etherscan, insert the address, see the first transactions. They will be right at the bottom of the page.
And here are the ones we need: 1, 2. The sender of the funds in the transaction table is always shown on the left of the IN (incoming transaction) or OUT (outgoing transaction) bar

So, we have identified the source of the funds, which is address 0xA474cE48300D91334339fb5aDeF99A1B11B1cfe6. What can we extract from this information?
In our case, the first address of the hacker, 0x8648... (aka Fake_Phishing5435 in the picture above) never received any funds before the transactions we detected. So address 0xa474... is the sponsor address (or funding address) with respect to the hacker address, or 0x8648..., or Fake_Phishing5435.
Most often the sponsor address is affiliated with a target address. The owner of the sponsor address could be, for example, some customer who has paid for services with crypto. Or, for example, the sponsor address is operated by a cryptocurrency exchange whose services are used by the owner of the target address.
But even more often, both the target address and the sponsor address have the same owner. Let's analyze the transactions of the sponsor address and try to figure out which option would be correct in our case.
The most interesting direction in the case of the sponsoring address is to try to detect suspicious transactions (such as the theft of NFT). To do this, open the address in Etherscan.io and go to "ERC-721 token Txns", which is the section responsible for NFT transfers.
 We see four transactions, two incoming, two outgoing. The first NFT, Mutant Ape Yacht Club (MAYC), was sold half an hour after receipt. The second, Azuki, 9 (!) minutes later. Seems suspicious to me!But how do we prove that these transactions are not a normal sale, but a real theft? By the consequences!In order to sell MAYC, you have to contact the Opensea marketplace's smart contracts. When you interact with them, the marketplace will automatically generate a profile for you, accessible via a link like "https://opensea.io/ETH_Address".I should also add that Opensea.io actively cooperates with law enforcers and also actively assists victims. In case of hacking, the stolen tokens are blocked and the hacker's account is banned, making his profile inaccessible.Let's try to open the profile of address 0xa474... and examine the transaction history. To do so, go to https://opensea.io/0xA474cE48300D91334339fb5aDeF99A1B11B1cfe6.
We see four transactions, two incoming, two outgoing. The first NFT, Mutant Ape Yacht Club (MAYC), was sold half an hour after receipt. The second, Azuki, 9 (!) minutes later. Seems suspicious to me!But how do we prove that these transactions are not a normal sale, but a real theft? By the consequences!In order to sell MAYC, you have to contact the Opensea marketplace's smart contracts. When you interact with them, the marketplace will automatically generate a profile for you, accessible via a link like "https://opensea.io/ETH_Address".I should also add that Opensea.io actively cooperates with law enforcers and also actively assists victims. In case of hacking, the stolen tokens are blocked and the hacker's account is banned, making his profile inaccessible.Let's try to open the profile of address 0xa474... and examine the transaction history. To do so, go to https://opensea.io/0xA474cE48300D91334339fb5aDeF99A1B11B1cfe6. oops! the address was banned.......We now know two facts about the sponsor address: it transferred money to the hacker's address, which was then used as a commission, and also made questionable transactions with NFT, for which it was banned from Opensea.io.
oops! the address was banned.......We now know two facts about the sponsor address: it transferred money to the hacker's address, which was then used as a commission, and also made questionable transactions with NFT, for which it was banned from Opensea.io.The target address also made questionable transactions with NFT and was banned from Opensea.io.
Now let's find out where the criminally obtained coins were sent to. To do this, let's examine the transactions in chronological order and try to find the incoming transactions immediately after the sale of (possibly) stolen NFTs. In this way, we will determine the amount of criminally acquired funds.The transactions we are looking for are found in the Internal Txns section:
 The hacker received a total of 23.8 ETH. To do this, let's examine the transactions in chronological form and try to find the incoming transactions immediately after the sale of (possibly) stolen NFTs. Who else sent the stolen coins to address 0x945b...? Target address!
The hacker received a total of 23.8 ETH. To do this, let's examine the transactions in chronological form and try to find the incoming transactions immediately after the sale of (possibly) stolen NFTs. Who else sent the stolen coins to address 0x945b...? Target address! Withdrawal transactions of stolen funds highlighted in yellow
Withdrawal transactions of stolen funds highlighted in yellowLet's find out what address 0x945b was used for... To do that, we again study the transactions in chronological order, we are interested in all incoming and outgoing transactions after the address received the stolen funds.
Target email address (13 ETH) was the first one to receive the stolen funds. Next, address 0x945b accumulated presumably stolen funds from several other addresses, including the target address. The money was then, as ZachXBT wrote, withdrawn to the Tornado.Cash mixer

The money sent to the mixer was grouped into two payments of 100 ETH, of which 125 ETH originally belonged to the target address, 13 ETH to the sponsoring address, and the remaining 62 ETH to other addresses.

It turns out that either the hacker owns all five addresses and uses 0x945b as an intermediate point before money laundering, or the owner of 0x945b is a separate criminal (money launderer) whose services are used by several criminals at the same time.
Let's briefly examine the other hacker addresses: as you can see from the graph, they too have interacted with NFT on Opensea. Let's use the old vetting method and... one of the addresses is in a ban on Opensea! The second address is not in the ban, but appears in the ZachXBT investigation. Here you can see the names and faces of our heroes, the dangerous cybercriminals.
 Mathys and Camille together
Mathys and Camille togetherWell here comes our friends Mathys and Camille from romantic France shitting themselves hard by posting a screenshot of one of their profiles on Opensea with previously stolen NFTs on their personal Twitter. This profile appears in our investigation, on the graph is address 0x5bb51...
Admittedly, I even got a little upset at this stage. How is it, we've only just started and they've already found everyone for us!But I decided not to dwell on Mathis and Kamila and go a bit further and try to add new factors to my investigation.Back to the sponsor address. The sponsor address, like most addresses on the Ethereum network, has its own sponsor address (pardon the recursion). Let's find it!
This time the sponsor address is signed in the block browser as Fake_Phsihing5099. Comments about the affiliation of all the addresses appearing in the investigation seem to me to be redundant with:
Having discovered the new sponsor address I decided to go towards the final destination of the funds and figure out exactly where Fake_phishing5099 was sending the dirty money.
After looking through all the transactions, I found an interesting address 0x27429f480a3E2a69D7E4D738EBc54AeB4096eb43.
The owner of this address, according to a thread on epicnpc.com, is spamming in Discord (Discord is where many of the victims received the phishing links).
Diwan Nuri (judging by the content of the thread, that's the name of the address owner) was so far-sighted and wise that he registered the forum account with his personal email. This wasn't enough, so he decided to screw one of his potential clients by sending them his ETH address in addition to the email.
This wasn't enough, so he decided to screw one of his potential clients by sending them his ETH address in addition to the email. According to the record we found, Diwan graduated from German Aletta-Haniel-Gesamtschule and now earns his living by spamming and scamming.So, after studying 6 cryptocurrency addresses and their transactions, we found out that:5-6 of the addresses in question were communicating with NFT.4 six analyzed addresses were involved in illegal activity and got banned at Opensea4 six investigated addresses were "skimming" for the withdrawal of funds to the Tornado.Cash mixer2/six of the addresses have been implicated in existing investigations6 addresses have close economic tiesThe couch is not as simple as it looks!In my opinion, the discovered facts are enough to merge the addresses into a cluster. Which addresses do we merge:
According to the record we found, Diwan graduated from German Aletta-Haniel-Gesamtschule and now earns his living by spamming and scamming.So, after studying 6 cryptocurrency addresses and their transactions, we found out that:5-6 of the addresses in question were communicating with NFT.4 six analyzed addresses were involved in illegal activity and got banned at Opensea4 six investigated addresses were "skimming" for the withdrawal of funds to the Tornado.Cash mixer2/six of the addresses have been implicated in existing investigations6 addresses have close economic tiesThe couch is not as simple as it looks!In my opinion, the discovered facts are enough to merge the addresses into a cluster. Which addresses do we merge:Target address 0x864875aef79B107221bEE89C8ff393BD2B66d96
Target Address 0xA474cE48300D91334339fb5aDeF99A1B11B1cfe6Hackers' complementary address #1 0x38dB16DA44A61560e04E94DCb71c3E64Aa94d318Hackers secondary address #2 0x5bb5180D8b84d754F56e2BC47Dc742d0f5Ac37FEThe laundering address 0x945b4a77649Ebe89eABAf03F78A0C8993f99bd41Fake_Phishing5099 0xdE09020653cA303CFC143d23A18183299558065FWhat can we learn after clustering the addresses together?
 First, our 'friends made about $1.7M on such a scam. One million was sent to the Tornado.Cash mixer.
First, our 'friends made about $1.7M on such a scam. One million was sent to the Tornado.Cash mixer. Second, just over $300k went to centralised exchanges (those with KYC procedures, cooperating with law enforcement, etc.). $285k went to Coinbase.Thirdly, we will get a much more detailed list of counterparties of this criminal group, which (as in the case of Couch, for example) can lead to interesting findings. And it could help law enforcement to trace the stolen money back to exchanges and exchanges.
Second, just over $300k went to centralised exchanges (those with KYC procedures, cooperating with law enforcement, etc.). $285k went to Coinbase.Thirdly, we will get a much more detailed list of counterparties of this criminal group, which (as in the case of Couch, for example) can lead to interesting findings. And it could help law enforcement to trace the stolen money back to exchanges and exchanges.Conclusions
As you can see from the material above, cryptocurrency is far from always anonymous. By properly applying OSINT and financial investigation techniques and methods, as well as knowing the theory of cryptocurrency, even large thefts can be successfully investigated, let alone small ones like the one we discussed today.What can we do concretely?Look for the source of the funds (sponsor address) and the final destination of the funds. Analyse in detail the transactions of each address in question.We can cluster the addresses based on this data. This may be done either within the software you are using, e.g. Cheynalisis, or logically.If the software you have available does not support clustering, I recommend exporting the transactions of the addresses you want from Etherscan.io and then merging multiple tables into one.After aggregating the addresses into a cluster, in our case we were able to understand the approximate volume of the thefts committed and also find out information about which exchanges the money from those thefts was being withdrawn to. We also learned that around a million dollars had been withdrawn to Tornado.Cash, which is a ready-made money laundering charge in some jurisdictions! -
ИНСТРУМЕНТЫ ДЛЯ OSINT 2022 (часть 2)
Первую часть списка, содержащую более 600 инструментов для OSINT, можно найти здесь>>
Браузерные расширения для OSINT
Поиск в двух разных поисковых системах доменов электронной почты и поиск в фотопоисковой системе других сервисов.
• Double Shot Search ( https://chrome.google.com/webstore/d...lhdnfdpdogdhop ) - это расширение для Chrome, которое удваивает ваш поиск. Вы можете искать одновременно в Bing и Google.
Найдите адреса электронной почты за считанные секунды
• Hunter (Email Hunter) ( http://hunter.io ) - сервис, который найдет адреса электронной почты, связанные с определенным доменом. Также с помощью этого инструмента можно найти адрес электронной почты по фамилии за пару секунд.
• RevEye ( https://chrome.google.com/webstore/d...nmpiklalfhelgf ) - расширение для Chrome с открытым исходным кодом, которое пробивает фотографию с помощью Google, Bing, Yandex и TinEye.
• Namechk ( https://namechk.com ) Username and Domain Name Checker - Search All Domain Names and User Names to see if they're available) - сайт, который найдет все аккаунты человека во всех социальных сетях и мессенджерах. Достаточно ввести его ник в одной социальной сети, и тот же ник будет найден в другой.
Поиск цели по IP и MAC-адресу - OSINT
Друзья, сегодня я подготовил для вас очень полезную подборку ресурсов, благодаря которым вы сможете найти информацию о вашей цели с IP или MAC адресом.
• HostHunter ( https://github.com/SpiderLabs/HostHunter ) • обнаруживает и извлекает имена хостов из набора целевых IP-адресов;
• Cyberhubarchive ( https://github.com/cyberhubarchive/archive ) - архив утечек данных, в нем есть IP-адреса аккаунтов Skype;
• Iknowwhatyoudownload (торрент-загрузки и раздачи для IP 54.91.109.76 http://iknowwhatyoudownload.com/ ) - показывает, что скачивается в Интернете;
• Recon ( https://recon.secapps.com/ ) - автоматический поиск и отображение ссылок;
• Извините. Вы не используете Tor. - найдет список всех исходящих узлов Tor за последние 16 часов, которые могли достичь IP;
• Reverse IP, NS, MX, WHOIS и Search Tools (https://dnslytics.com/reverse-ip ) - найдет домены;
• @iptools_robot - бот для быстрого поиска информации об ip адресах, найдет whois, реальный IP за Cloudflare, порты и многое другое;
• Welcome to Tor Metrics ( http://metrics.torproject.org ) - проверяет, использовался ли IP-адрес в качестве хоста для Tor-трафика, требует дату;
Компиляция сервисов для компьютерной разведки OSINT
Список сервисов и утилит, созданных для анализа таких данных, как IP, SSID, метаданные файлов, записи DNS и всего, где объектом анализа является элемент IT-структуры, будь то сайт или IP-адрес.
• Whatsmydns ( https://www.whatsmydns.net/ ) - проверка DNS записей сайта (включая скрытые).
• dns recon and research, find and lookup dns records ( http://dnsdumpster.com/ ) - Данные о сайте, включая местоположение хостинга и владельца, а также другие данные.
• xinit.ru ( https://xinit.ru/bs ) - проверка домена или IP-адреса по whois; получение снимков из кэша Google и данных из веб-архива; сервисы и протоколы на сервере; заголовки ответов HTTP; ссылки со страниц сайта на хосте; адреса электронной почты домена; проверка сайта на VirusTotal; показ реального IP-адреса за Cloudflare; DNS-инфраструктура сайта.
• URL и сканер сайтов ( http://urlscan.io/ ) - проверяет, кому выдан TLS-сертификат и какие IP-адреса связаны с сайтом.
• PDFCandy ( https://pdfcandy.com/edit-pdf-meta.html ) - сервис дает возможность извлекать и изменять метаданные PDF.
• Wigle ( https://wigle.net/ ) - может показать SSID и BSSID точек доступа Wi-Fi на карте.
• PublicWWW ( http://publicwww.com/ ) - сервис осуществляет поиск исходного кода страниц. Находит никнеймы, ссылки в коде, совпадающие иконки сайтов, что позволяет искать двойников; находить любые похожие ID или фразы, кошельки, токены, также позволяет находить поставщиков рекламных виджетов и т.д.
• Metadata2Go ( https://www.get-metadata.com ) - помогает узнать все метаданные файла.
• HostHunter ( https://github.com/SpiderLabs/HostHunter ) - поиск доменных имен по набору IP-адресов.
• Knock Subdomain Scan ( https://github.com/guelfoweb/knock ) - перебирает поддомены на целевом домене и может генерировать выходной файл с результатами.
Поиск данных человека по номеру банковской карты - OSINT.
Бывают ситуации, когда нас обманывают мошенники, имея на руках только номер карты.
Поиск через мобильный банк
Мы пытаемся сделать перевод через мобильное приложение нашего банка. В этом случае желательно, чтобы и вы, и объект поиска пользовались одним и тем же крупным банком, например, Сбером.
Но здесь это вопрос везения.
Если звезды сошлись, банковский интерфейс выдаст нам имя владельца карты.
Поиск через специальные сервисы
В сети существуют десятки сервисов, позволяющих найти конкретную информацию по номеру карты.
Это может быть название банка, тип карты или регион проживания владельца.
• bincheck.io ( https://bincheck.io )
• bincheck.org ( https://bincheck.org/ )
• freebinchecker.com (https://www.freebinchecker.com )
Этот сервис позволяет проверить тип вашей кредитной дебетовой карты и другие данные.
• binlist.net ( https://binlist.net )
• psm7.com ( https://psm7.com/bin-card )
Проверка биткоин кошелька - OSINT[/color]
Уже ни для кого не секрет, что биткоин не так анонимен, как многие думают. Баланс кошелька и все его переводы можно легко отследить. Именно поэтому существует список некоторых сервисов, которые могут помочь в этом.
• Bitref ( https://bitref.com ) - Верификация биткоин-кошелька.
• Block Explorer ( https://blockexplorer.com ) - Block Explorer, позволяет отслеживать, куда и когда уходят деньги с вашего биткоин-кошелька.
• Blockchain ( https://www.blockchain.com/ru/explorer ) - Block Explorer, также позволяет отслеживать транзакции в вашем кошельке.
• Cryptocurrency Alerting ( https://cryptocurrencyalerting.com/wallet-watch.html ) - Сервис, позволяющий устанавливать уведомления об активности вашего адреса.
• Blockseer ( https://www.blockseer.com ) - Визуализация связей между адресами, участвующими в транзакциях.
Вычисление жертвы по фотооснове.
• Photo Sherlock ( https://t.me/BrainHaking2_0ENG/72 ) - Приложение обеспечивает поиск фотографий из камеры или галереи. С его помощью можно найти информацию о фотографии в Интернете, например, проверить, кому на самом деле принадлежит фотография из социальной сети (проверка на поддельные изображения).
Модификация получила Premium, убрана реклама и мусор. Незаменимая вещь для любого OSINT'ера.
• Search4faces.com ( https://search4faces.com )- бесплатный сервис для поиска лиц в социальных сетях. В настоящее время существует 4 базы изображений:
1 миллиард 109 миллионов 563 тысячи аватаров VK.com;
280 миллионов 781 тысяча аватаров из Vk.com + Odnoklassniki.com;
125 миллионов 443 тысячи аватаров из TikTok;
4 миллиона 594 тысячи аватаров от ClubHouse;
Поиск можно осуществлять не только по фотографии, но и по любому другому изображению человеческого лица. Например, по фотографии или фотороботу.
-
OSINT TOOLS 2022 (Part 2)
Browser extensions for OSINT
Search two different search engines for email domains and search photo search engine for other services.
• Double Shot Search ( https://chrome.google.com/webstore/detail/double-shot-search-query/kddlkbpbepnaepdleclhdnfdpdogdhop ) is a Chrome extension that doubles your search. You can search on both Bing and Google at the same time.
Find email addresses in seconds
• Hunter (Email Hunter) ( http://hunter.io ) a service that will find e-mail addresses associated with a particular domain. Also, you can use this tool to find an email address by last name in a couple of seconds.
• RevEye ( https://chrome.google.com/webstore/detail/reveye-reverse-image-sear/keaaclcjhehbbapnphnmpiklalfhelgf ) is an open-source Chrome extension that punches in a photo using Google, Bing, Yandex and TinEye.
• Namechk ( https://namechk.com ) Username and Domain Name Checker - Search All Domain Names and User Names to see if they're available ) is a site that will find all the accounts of a person in all social networks and messengers. It is enough to enter his nickname in one social network and the same nickname will be found in the other one.
Finding a Target by IP and MAC Address - OSINT
Folks, today I have prepared for you a very useful collection of resources, thanks to which you can find information about your target with IP or MAC address.
•HostHunter ( https://github.com/SpiderLabs/HostHunter ) - Discovers and extracts host names from a set of target IP addresses;
•Cyberhubarchive ( https://github.com/cyberhubarchive/archive ) - archive of leaked data, it has IP addresses of Skype accounts;
Iknowwhatyoudownload (Torrent downloads and distributions for IP 54.91.109.76 http://iknowwhatyoudownload.com/ ) - shows what is being downloaded online;
•Recon ( https://recon.secapps.com/ ) - automatic search and link mapping;
•Sorry. You are not using Tor. - will find a list of all Tor outbound nodes in the last 16 hours that could reach an IP;
•Reverse IP, NS, MX, WHOIS and Search Tools (https://dnslytics.com/reverse-ip ) - will find domains;
•@iptools_robot - bot to quickly find ip address information, will find whois, real IP behind Cloudflare, ports and more;
•Welcome to Tor Metrics ( http://metrics.torproject.org ) - checks if the IP address was used as a host for Tor traffic, requires a date;
Compilation of services for OSINT computer intelligence
List of services and utilities created for analysis of such data as IP, SSID, file metadata, DNS records, and everything where the object of analysis is an element of IT structure, be it a site or IP address.
•Whatsmydns ( https://www.whatsmydns.net/ ) - Check DNS records of the site (including hidden ones).
•dns recon and research, find and lookup dns records ( http://dnsdumpster.com/ ) - Site data including hosting location and owner location, as well as other data.
•xinit.ru ( https://xinit.ru/bs ) - check domain or IP address by whois; get snapshots from Google cache and data from web archive; services and protocols on server; HTTP response headers; links from site pages on host; email addresses of domain; check site on VirusTotal; show real IP address behind Cloudflare; DNS infrastructure of site.
•URL and website scanner ( http://urlscan.io/ ) - checks who is issued a TLS certificate and which IP addresses are associated with the site.
•PDFCandy ( https://pdfcandy.com/edit-pdf-meta.html ) - service gives you the ability to extract and modify PDF metadata.
•Wigle ( https://wigle.net/ ) - can show you the SSID and BSSID of the Wi-Fi hotspots on the map.
•PublicWWW ( http://publicwww.com/ ) - service searches the source code of pages. Finds nicknames, references in code, matching website icons, that allows looking for twins; find any similar IDs or phrases, wallets, tokens, also allows finding advertising widgets providers, etc.
•Metadata2Go ( https://www.get-metadata.com ) - helps to find out all the metadata of a file.
•HostHunter ( https://github.com/SpiderLabs/HostHunter ) - searches domain names for a set of IP addresses.
•Knock Subdomain Scan ( https://github.com/guelfoweb/knock )- Crawls subdomains on the target domain and can generate an output file with results.
Looking for a person's details from a bank card number - OSINT.
There are situations where we get scammed by fraudsters with only the card number in hand.
Search through mobile banking
We try to make a transfer through our bank's mobile application. In this case, it is desirable that both you and the object of the search used the same major bank such as Sber.
But here it is a matter of luck.
If the stars are aligned, the banking interface will give us the name of the cardholder.
Search through special services
There are dozens of services on the net that allow you to find specific information by card number.
It can be a name of a bank, a type of card or a region the owner lives in.
•bincheck.io ( https://bincheck.io )
•bincheck.org ( https://bincheck.org/ )
•freebinchecker.com (https://www.freebinchecker.com )
This service allows you to check your credit debit card type and other details.
•binlist.net ( https://binlist.net )
•psm7.com ( https://psm7.com/bin-card )
Bitcoin Bitcoin wallet checker - OSINT
It is no longer a secret that bitcoin is not as anonymous as many people think. The balance of a wallet and all of its transfers can easily be tracked. That's why there is a list of some services that can help with this.
•Bitref ( https://bitref.com ) - Bitcoin wallet verification.
•Block Explorer ( https://blockexplorer.com ) - Block Explorer, allows you to track where and when your bitcoin wallet's money goes.
•Blockchain ( https://www.blockchain.com/ru/explorer ) - Block Explorer, also allows you to track transactions in your wallet.
•Cryptocurrency Alerting ( https://cryptocurrencyalerting.com/wallet-watch.html ) - Service allowing you to set notifications about activity of your address.
•Blockseer ( https://www.blockseer.com ) - Visualisation of links between addresses involved in transactions.
Picking up the victim by photo-OSINT.
•Photo Sherlock ( https://t.me/BrainHaking2_0ENG/72 ) - The application provides a photo search from the camera or gallery. You can use it to find information about a picture on the Internet, for example to check who really owns a photo from a social network (check for fake images).
The modification got Premium, removed ads and rubbish. An indispensable thing for any OSINT'er.
•Search4faces.com ( https://search4faces.com )- free service for searching faces in social networks. Currently there are 4 image bases:
1 billion 109 million 563 thousand VK.com avatars;
280 million 781 thousand avatars from Vk.com + Odnoklassniki.com;
125 million 443 thousand avatars from TikTok;
4 million 594 thousand avatars from ClubHouse;
You can search not only by photo but also by any other image of a human face. For example, from a picture or a sketch.
Get one-touch information about a picture on the Internet!
-
Anonymity and emergency data deletion for smartphones.
Anonymity and emergency data deletion for smartphones.
Privacy Extensions for Android (Compilation #1).

1. NetGuard (https://netguard.me/)-allows you to see which applications are sending data and where, and to block unwanted data sending. The application does not require root access and allows to block connections for both user and system applications. Source code.
2. Orbot (https://guardianproject.info/apps/orbot/) - allows you to use the Tor anonymous network on Android and redirect traffic from other applications, including the browser, mail, maps, etc. A great extension to improve your privacy on the web. Source code.3. XPrivacyLua (https://lua.xprivacy.eu/) - an easy to use "privacy manager" XPrivacyLua solves the problem of excessive application permissions in an interesting way: instead of directly denying access (which often leads to application stopping), it sends fake data instead of the real data, providing user privacy. Source code.Emergency smartphone cleaning apps (Compilation #1).
 For some, the smartphone is life. The plastic box holds so much sensitive information that a blackmailer can "overdose". There's no need to feel sorry for him, but it's advisable to feel sorry for yourself! What's the point? Password as the only means of protection - it doesn't work.It should be so the phone is in the wrong hands - the files are deleted.
For some, the smartphone is life. The plastic box holds so much sensitive information that a blackmailer can "overdose". There's no need to feel sorry for him, but it's advisable to feel sorry for yourself! What's the point? Password as the only means of protection - it doesn't work.It should be so the phone is in the wrong hands - the files are deleted.1. AutoWipe (https://4pda.to/forum/index.php?showtopic=230102&st=0) - full wipe is done, if unlock password is entered incorrectly several times.
2. SecAddon (https://github.com/zalexdev/securityaddon/releases/download/7.0-BETA/SecAddon+7+BETA.apk) - deletes or encrypts files, which user selected beforehand in unforeseen circumstances.3. Ripple (http://github.com/guardianproject/ripple) - "panic button" to trigger a "ripple effect" in all applications that are configured to respond to panic events.Change MAC Address on Android (Link>>>>)
 This program on Android, allows you to change your device's MAC address to a random one, or one that you prescribe.
This program on Android, allows you to change your device's MAC address to a random one, or one that you prescribe.Usage (as an option):
1. Scan your network with any network sniffer program2. Copy a couple of MAC addresses3. Change MAC address to another one in the program4. Log onto the network only when the original is logged out.Or just hide your MAC addressRoot is required to use the software!
Image metadata removal app for Android.
 Scrambled Exif (https://f-droid.org/en/packages/com.jarsilio.android.scrambledeggsif/)-App for removing metadata from photos before submitting them. For Android users
Scrambled Exif (https://f-droid.org/en/packages/com.jarsilio.android.scrambledeggsif/)-App for removing metadata from photos before submitting them. For Android usersA cleanup app for your smartphone with no data recovery option.
 Extirpater (https://f-droid.org/packages/us.spotco.extirpater/) is a cleaning app for your smartphone without the possibility of data recovery.
Extirpater (https://f-droid.org/packages/us.spotco.extirpater/) is a cleaning app for your smartphone without the possibility of data recovery.This is usually needed before selling your smartphone. A standard factory reset does not guarantee complete deletion of your data, in particular photos.
Extirpater cleans everything once and for all, as it uses an alternative way of deleting data: it fills the remaining space on your smartphone with random files and deletes everything at once without the possibility of recovery.
https://www.advisor-bm.com/post/anonymity-and-emergency-data-deletion-for-smartphones -
Анонимность и экстренное удаление данных для смартфонов

Расширения приватности для Android (Подборка №1).
1. NetGuard (https://netguard.me)— позволяет увидеть, какие приложения и куда отправляют данные, а также заблокировать нежелательную отправку данных. Приложение не требует рутового доступа и позволяет блокировать соединения как для пользовательских, так и для системных приложений. Исходный код.
2. Orbot (https://guardianproject.info/apps/orbot/)— позволяет использовать анонимную сеть Tor на Android и перенаправлять через нее трафик от других приложений, в т.ч. браузера, почты, карт и т.д. Отличное расширение для повышения приватности в сети. Исходный код.
3. XPrivacyLua (https://lua.xprivacy.eu) — простой в использовании "менеджер приватности" XPrivacyLua решает проблему избыточных разрешений приложений интересным способом: вместо прямого запрета на доступ (что часто приводит к остановке приложений), он отправляет фейковые данные взамен настоящих, обеспечивая пользовательскую приватность. Исходный код.
Приложения для экстренной очистки смартфона (Подборка №1).
Для кого-то смартфон — жизнь. В пластиковой коробочке хранится так много конфиденциальной информации, что шантажист может «схватить передоз». Его жалеть не нужно, а вот себя — очень желательно! К чему ведём? Пароль как единственное средство защиты — это не работает.

Должно быть так телефон попал в чужие руки — файлы удалились.
1. AutoWipe (https://4pda.to/forum/index.php?showtopic=230102&st=0) — делается полный wipe, если пароль для разблокировки несколько раз введён неправильно.
2. SecAddon (https://github.com/zalexdev/securityaddon/releases/download/7.0-BETA/SecAddon+7+BETA.apk) — в непредвиденных обстоятельствах удаляет или шифрует файлы, которые пользователь выбрал заранее.
3. Ripple (http://github.com/guardianproject/ripple) — «тревожная кнопка» для запуска «эффекта пульсации» во всех приложениях, которые настроены реагировать на панические события.
Смена MAC-Адреса на Android (Ссылка>>>>)
Данная программа на Android, позволяет менять MAC-адрес вашего устройства на рандомный, или тот, который вы пропишете.Использование (как вариант):
1. Сканируем сеть любой программой для анализа сети
2. Копируем парочку MAC адресов
3. Меняем MAC в программе на чужой
4. Заходим в сеть только, когда оригинал выйдет из нее.
Или просто скройте свой MAC адрес
Для использования софта Root обязателен!
Приложение для удаления метаданных с картинки для Android.
 Scrambled Exif
Scrambled ExifScrambled Exif (https://f-droid.org/en/packages/com.jarsilio.android.scrambledeggsif/)— приложение для удаления метаданных с фотографий перед их отправкой. Для пользователей Android.

Приложение для чистки для вашего смартфона без возможности восстановления данных.
Extirpater (https://f-droid.org/packages/us.spotco.extirpater/) — приложение для чистки для вашего смартфона без возможности восстановления данных.
Обычно это нужно перед продажей смартфона. Стандартный заводской сброс не гарантирует полного удаления ваших данных, в частности, фотографий.
-
Blockchain.com blocked cryptocurrency withdrawal, fraud or Decentralization vs centralized finance!

Blockchain.com blocked the withdrawal of funds for the citizens of the Russian Federation, while making it impossible to provide documents confirming a change of citizenship or residence in another country.
But the most interesting thing is that citizens of other countries, such as India, Mexico, Argentina, Kazakhstan, Thailand, Ukraine, Azerbaijan and even Canada............ fell under this "wave".Judging by the complaints, everyone has different reasons, someone to re-verify, someone to confirm the legitimacy of funds in the purse, some just without explanation.And it looks very strange that after all confirmation of the origin of funds and verification, some citizens of India are asked a separate withdrawal fee...The situation, to put it mildly, is strange, according to experts, the blocked amount is estimated at millions of dollars, and judging by the behavior of Blockchain.com they are very eager to part with this amount.Similar cases have occurred before, but they have never been of such massive volume. Now the whole crypto market is wondering if this is too zealous implementation of the law, or we will see Blockchain.com as a new participant in our list of scams : Top Scam Crypto Projects! We would like to point out from ourselves:
Now the whole crypto market is wondering if this is too zealous implementation of the law, or we will see Blockchain.com as a new participant in our list of scams : Top Scam Crypto Projects! We would like to point out from ourselves:Service "purse" blockchain.com - it's just an interface, and nothing more (well and a little "strange" administration of the project).
If you have seed phrase or private key of your wallet on blockchain.com, you can easily withdraw your cryptocurrency through other wallets.And no "either scams or bans" will not become an obstacle here, it's just technically impossible.In general, we are very sorry that blockchain and crypto-market, becomes similar to regulated financial system, where everything depends on the mood of specific individuals, and on the agreements of certain financial institutions.Blockchain and cryptocurrencies became what they are because they were independent from external factors, but the market is flooded by centralized projects....
At the same time, it should be noted that now the market is clearly turned in the direction of DEX, and decentralized projects have already come out ahead.Perhaps, it is the negative consequences for the centralized market of actions like Blockchain.com that will turn the blockchain industry in the direction of decentralization and return the market to the right "rails".Ethereum founder Mr. Buterin's owl comes to mind, referring to both centralized exchanges and other centralized blockchain projects.
 "I definitely personally hope that centralized exchanges burn in hell:"In turn, we recall the types of wallets:
"I definitely personally hope that centralized exchanges burn in hell:"In turn, we recall the types of wallets:NOT RECOMMENDED FOR USE:
A custodial wallet (centralized) is a service that stores the wallet's private key, and its "owner" performs transactions exclusively through this service. As a rule, this requires KYC (Know Your Customer).Such wallets are primarily used on cryptocurrency exchanges, which belong to the type of centralized exchanges. RECOMMENDED FOR USE:Non-custodial wallet (Decentralized): differs in the fact that the private key or seed phrase is stored or directly with the owner, and for its creation and use there is no need to go through any identification procedures, i.e. there is simply no identification data about the owner of such a wallet.In this case, it is de facto impossible to restrict its use, you can send a transfer/payment to the address of another crypto wallet directly, and if you need to exchange transactions, use DEX - a decentralized type of exchanges.For this type of wallet there is no possibility to limit transactions, (although some decentralized exchanges can implement KYC).Also we urge you to remember about security (read manuals about cold wallets) remember in real blockchain only you are responsible for your funds!
RECOMMENDED FOR USE:Non-custodial wallet (Decentralized): differs in the fact that the private key or seed phrase is stored or directly with the owner, and for its creation and use there is no need to go through any identification procedures, i.e. there is simply no identification data about the owner of such a wallet.In this case, it is de facto impossible to restrict its use, you can send a transfer/payment to the address of another crypto wallet directly, and if you need to exchange transactions, use DEX - a decentralized type of exchanges.For this type of wallet there is no possibility to limit transactions, (although some decentralized exchanges can implement KYC).Also we urge you to remember about security (read manuals about cold wallets) remember in real blockchain only you are responsible for your funds!I will not advertise specific names of crypto wallets, you will find a lot of reviews on the Internet.
But remember, when you make transactions with cryptocurrency inside blockchain network, without withdrawing funds to fiat currencies (USD, EUR and others), and you are already asked for KYC, run away from such service, it seems you got not on blockchain marketblockchain, but in some "bank or similar structure" which is just hiding behind the word blockchain.Decentralization vs. centralization: where is the future?
What do you think?
Original text, learn more! -
600 BEST OSINT TOOLS 2022.
The first OSINT service with artificial intelligence using more than 1100 sources of information "OSINT AI BM".
There are 7 months to go until the service is launched.
We decided to make available to you some of the information sources that you can use for OSINT.
Link to original resource list>>>>
Keyword research tools.

-
One Look: Enter a word, phrase, sentence, or pattern to search for related words.
-
Ubersuggest: suggest keywords not available in the Google Keyword Planner.
Browser extensions for OSINT.

-
Double Shot Search is an extension for Chrome that doubles the search. It searches in two search engines simultaneously - Bing and Google.
-
Hunter.io is a service that will find e-mail addresses associated with a certain domain. You can also use this tool to find an e-mail address by name in a couple of seconds.
-
RevEye is an open-source Chrome extension that runs a photo through Google, Bing, Yandex and TinEye.
Search Engines. General Search
-
Google Bing Yahoo AOL Infospace Lycos Exalead ASK Ecosia entireweb teoma yippy
-
I Search From: simulate using Google Search from a different location or device, or perform a search with custom search settings.
-
millionshort: Allows you to remove the top of the search engine results (e.g Remove top 100,1000,10000)
National Search Engines.

Privacy-oriented search engines

-
DuckDuckGo: Online investigators usually use it to search the surface web while using the Tor Browser.
-
Startpage: Fetch results from Google without tracking its users.
-
Peekier: Privacy oriented search engines that fetch its results using its own search algorithm.
-
Qwant: Based in France.
-
Oscobo: Based in UK.
-
Swisscows: Privacy safe WEB-search based in Switzerland.
-
Gigablast: Open source search engine.
-
Gibiru: Uncensored and anonymous search engine.
Meta search engines

-
etools: Compile its results from major international search engines, keep user privacy by not collecting or sharing personal information of its users. This search engine is very fast and show a summary for each search query -on the right side- detailing the source of its results.
-
All the interne: query major search engines including shopping site like Amazon and eBay.
-
izito: Aggregate data from multiple sources (Yahoo, Bing, Wikipedia, YouTube and other) to generate optimal results which includes images, videos, news and articles.
-
Metacrawler: Aggregate results from Google and Yahoo!.
-
My all search: Aggregates results through Bing, DuckDuckGo, AOL Search, Ask, Oscobo, Mojeek, ZapMeta, MetaCrawler.
-
Carrot2: Open Source Search Results Clustering Engine aggregate results from GoogleAPI, Bing API, eTools Meta Search, Lucene, SOLR, and more.
-
elocalfinder: Fetch results from Google, Yahoo!, Ask and Bing .
Files Search Engines
-
grayhatwarfare: Search for Open Amazon s3 Buckets and their contents.
There are specialized sites that hold images appeared in the press and news media, to search for this type of images go to:

-
Gettyimages: Contains images from news, entertainment, fashion, sports and archival imagery.
Images shared across social media sites can be found in the following locations:
-
idGettr: Find Flicker ID number (also works for groups).
-
Flickr Hive Mind: Data mining tool for the Flickr database of photography.
-
Stalkture: Instagram Online Web Viewer.
There are specialized sites that hold images appeared in the press and news media, to search for this type of images go to:
-
Cam finds App: this is an App available for both Android and Apple devices. It uses visual search technology to recognize uploaded picture and give instant results about it like related images, local shopping results and a vast selection of web results.
Graphics search:
Stock photo search:
Video Search Engines-
Geo Search Tool: Search for all movies according to a specific query entered by the user – the result set will be further filtered according to the distance from a specific location (city, village, intersection) and according to a specific time frame (past hour, past two or three hours ..etc.).
Blog Search.-
Bloghub: Online blog directory.
Fake News Detection.
-
Snopes: Discovers false news, stories, urban legends and research/validate rumors to see whether it is true.
-
Hoaxy: Check the spread of false claims (like a hoax, rumor, satire, news report) across social media sites. The site derives its results from reputable fact checking organizations to return the most accurate results.
-
FactCheck: This site is partnered with Facebook to help identify and label fake news reported by its users. It also monitors different media for the false info covering a wide range of topics like health, science, hoaxes spread through Spam emails.
-
ReviewMeta: Analysis Amazon user reviews.
-
Reporter Lab: Gives a map of global fact-checking sites.
-
Truth Or Fiction: Discover fake news in different topics like politics, nature, health, space, crime, police and terrorism…etc.
-
Hoax-Slayer: Focuses on email scam and social media hoaxes.
-
Verification Handbook: A definitive guide to verifying digital content for emergency coverage available in different languages.
-
Verification junkie: This is a directory of tools for verifying, fact checking and assessing the validity of eyewitness reports and user self-published content online.
-
citizen evidence: tools and lessons to teach people how to authenticate user-generated online contents. Managed by Amnesty International.
News/Newspaper Search Engines.

-
1stHeadlines: Breaking news headline.
-
Newspaper Archives: Contains Newspaper Archives 1607-2017 and Obituaries & Family History Records.
-
Findmypast: US and world historical( China, Denmark, France, Germany, Jamaica, and South Africa are also searchable within the collection) Newspaper archive.
-
Newsography: International relations and armed conflicts global news aggregator and historical database.
-
Online Newspapers: Online Newspaper Directory for the World.
-
YouGotTheNews: Search Engine for US News – Search thousands of national, business, and local news sources.
-
Library of Congress Newspapers directory & 100 Years Ago Today: Search U.S. Newspaper Directory, 1690-Present using these two links from the Library of Congress.
Patent Search Engines

-
State Intellectual Property Office (SIPO) of the People’s Republic of China
-
stopfakes: The International Trade Administration (ITA), U.S. Department of Commerce, manages STOPfakes.gov to assist U.S. businesses protect and enforce their intellectual property rights against counterfeits and pirated goods in the global marketplace.
-
FreePatentsOnline: Patent metadata search engine.
Business Search
Business Profiles
-
Open corporates: The largest open database of companies in the world.
-
Zoom info: List companies in the U.S categorized by industry and offer information
-
corporationwiki: Allows you to search for any company and visualize the connection between people working within it
-
Kompass: This is a global B2B portal with information about companies in more than 60 countries.
-
Manta: Business directory for U.S businesses
-
LittleSisThis is a powerful profiling website that lists a wealth of information about 185,000 people and 67,000 organizations in varying stages of completion.
Business Annual Records

-
Annual Reports: Lists thousands of annual records from 5,333 companies worldwide.
-
Reporter Link: Contains more than 60 Million searchable tables, figures and datasets.
-
Company registration around the world: Give a list of government, commercial registers websites around the globe.
Data Leak Websites- GlobaLeaks: is an open-source, free software intended to enable secure and anonymous whistleblowing initiatives
-
Have I Been Facebooked? : Check if your data was part of the Facebook April 2021 breach.
-
Have I Been Zucked? : Check if your details are included in the 2019 Facebook data breach.
Pastebin sitesSocial Media IntelligenceFacebook
-
Facebook scanner: As of June 6th, you can scan only your own profile with this tool.
-
Socmint: Facilitate fetching information using Facebook Graph search.
-
Lookup ID: Find Facebook personal numeric ID / Group ID / Page ID.
-
FindMyFbid: Locate Facebook personal numeric ID.
-
LikeAlyzer: Analyze and monitor Facebook Pages.
-
Face Live: Facebook live video search.
-
Who posted what?: Facebook keyword search generator. It searches Facebook posts and limit the results to specific date.
-
ExtractFace: Automate extracting data from Facebook profiles (Not working currently).
Twitter
-
All My Tweets: View all public tweets posted by any Twitter account on one page.
-
Trendsmap: Shows you most popular trends, hashtags and keywords on Twitter from anywhere around the world.
-
Foller: Analysis Twitter account (profile public information, number of tweets and followers, topics, hashtags, mention).
-
First Tweet: Find the first tweet of any search keyword or link.
-
Social bearing: Analysis twitter accounts.
-
Sleeping Time: Predict the sleeping schedule of anyone on Twitter.
-
Simple Twitter Profile Analyzer (Python script).
-
Tag board:Search for hashtags on Twitter, Facebook & Google+.
-
Spoonbill: Monitor profile changes from the people you follow on Twitter.
-
Export Tweet: Advanced Twitter analytical service, you can download the generated report for off-line usage. To unlock full features, you need to pay.
LinkedIn
-
LinkedIn Scraper: Scrapes Any LinkedIn Data
-
Lisearcher: Easily find public LinkedIn profiles for candidates or B2B prospects in Google by searching using job title and keywords with boolean search.
Instagram
-
picodash: A powerful search engine to explore Instagram & Twitter photos, videos, users and locations.
Reddit
-
reddit-user-analyser.netlify.app: Analyse a Reddit user
-
resavr: Reveal Deleted Reddit Comments
-
redditsearch: Advanced Reddit search
-
karmadecay: Reverse image search of Reddit.com (beta)
-
Redective: The Reddit Search Detective
-
Mostly Harmless: looks up the page you are currently viewing to see if it has been submitted to reddit.
-
Reddit Enhancement Suite: A Google Chrome Add-on.
-
reddit investigator: Investigate Reddit users.
-
reddit metrics: a tool for tracking statistics of reddits users and discovering the fastest growing communities on reddit.
-
atomiks: Analyse a Reddit user.
-
SnoopSnoo: Get insights on any reddit user activity.
-
Reddit Comment Search: Search through comments of a particular reddit user.
Social Media Psychological Analysis
-
Tone Analyzer: This is an online service that offers free linguistic analysis to detect human feelings -like joy, fear, sadness, anger, analytical, confident and tentative tones- found in text – like Tweets, emails and Facebook messages.
-
Watson Tone Analyzer: This is a cloud based server created by IBM, it analyzes emotions and tones in online contents (e.g. Facebook posts, reviews and Tweets) to predict the emotional status of the writer. This service can be used in different scenarios -other than intelligence- like detecting customers tones to understand their needs or to better serve them.
-
Fake Sport: This site analyzes Amazon, Yelp, TripAdvisor and Apple App store users reviews to check The credibility of these reviews.
-
Review Meta: Investigate user reviews on Amazon to check which one is likely to be fake or misleading.
People Search

General People Search Engines
-
Truth finder: TruthFinder has a huge database of social media profiles, address history, contact information, public records (federal, country and state data sources) and other commercial sources, you can search using target first and/or last name in addition to city/state where he lives or lived before.
-
411: Search for people within the United States, search parameter includes Full name, location, reverse phone lookup, email and business.
-
People Smart: Search for people using thier name, phone, address or email.
-
Zaba Search: Find people in the USA using name or phone number.
-
White Pages: Search for people within the USA using their name, phone number, business or address.
-
Been Verified: Search for people within USA using their name, phone, email or mailing address.
-
Address Search: Search for someone email or mailing address using his name and location, the service is limited to the United States only.
-
Lullar: Search social media websites using target email address or first & last name or username.
-
Anywho: Finding people , places and businesses. You can search by name, address or phone number.
-
intelius: People search and phone number lookup.
-
Snoop Station: Search for people using full name and location. Commercial service.
-
Cubib: Search millions of online data records for free. Aggregated data is derived from people search, marketing data, property records, vehicle records, court records, patents, business registration, domain name registration, and white house visitation records.
-
Sorted By Name: A list of links to genealogy details -based on the first letter of the person’s surname- mentioned on other websites.
Online Registries

-
The Knot: Find a couple’s wedding registry and website.
-
Registry Finder: Search for registries.
-
My Registry: Global online gift registry service.
User Name Check
-
Check user name: Check the use of a specific username on 160 Social Networks, very useful to discover target social media accounts if he/she was using the same username on multiple platforms.
-
Namechk: Check to see if a specified username is used for major domain names and social media sites.
-
Namecheckr: Check domain & social username availability across multiple networks.
-
User Search: Scan 45 popular social media websites.
Email Search

Email validation services. This service checks whether an email address exists or not and gives other detailed technical information about it.
-
Email Permutator+: useful to guess the possible combination of the email account of the target.
-
Email Dossier: Give detailed technical validation report about emails.
-
Email Checker: Verify whether an email address is real.
-
Email Header AnalysisGet detailed technical information extracted from email headers, this includes sender IP address, email, sender ISP in addition to Geographical information.
Phone Number Search

-
Z lookup: International reverse phone lookup including cell phones.
Employee Profile

-
Recruit in: A third party website that use Google to search the profiles on LinkedIn. This return deeper results compared to LinkedIn.
-
Byte: Popular Middle east job website.
-
Xing: Business networking site
Government Records

Vital Records
These are government records usually created by local authorities, it includes birth and death records, marriage licenses and divorce decrees
-
genealogybank: Genealogy Records found in Newspapers such as: Birth Announcements, Engagements, Marriage, Anniversary & Divorce Records, Obituaries, Legal Notices, Family Reunions, Military Records
Passenger Lists, Photographs & Images, Shipping & Shipping Records, Community News Articles and more! -
Sorted By Birth Date: This site uses the Death Master File as of 1 March 2014.
-
U.S., Department of Veterans Affairs BIRLS Death File, 1850-2010
-
National Records of Scotland: Links to Births, Deaths and Marriage government records
in Scotland and selected countries like USA and Canada.
Criminal & Court Records
-
SpotCrime: Show a map of crime hot spots for hundreds of different cities around the United States.
-
The Inmate Locator: List inmate locator services in the United Sates.
-
National Criminal Justice Reference Service: This is federally funded resource offering justice and drug-related information to support research, policy, and program development worldwide.
Property Record
-
Zillow: Offers buying, selling, renting, financing, remodeling properties in the United States.
Tax & Financial Records
-
United States Public Records Online Directory: Contain links to official States Websites Public Databases including US citizens’ public tax records.
Social Security Number Search

-
SSN Check: Reverse Social Security Number Lookup (For USA only).
-
SSN-Verify: Social Security Number search and lookup tools.
Other Public Records
There are other types of online public records that can prove useful in some cases.
-
Search Systems: Public records search engine; it includes links to premium databases (require payment).
-
Federal Election Commission: List Individual contribution made by individuals, Native American tribes, partnerships, sole proprietorships, limited liability companies (LLCs) and contributions by the candidate to all political committees.
-
Follow That Money: How money spent in Federal elections.
-
Political Money Line: Track money spent in politics.
Local libraries in USA offer access to proprietary databases like ReferenceUSA (huge directory service) and America’s Newspapers (full-text obituaries) for a small fee. In many instances, such services can be offered remotely in exchange for a valid library subscription card.
Technical Footprinting
Website history
-
Cached pages:Show previous websites capture on three different archive websites (Google cache, Coral, Archive.org).
-
CachedView: The Google Cache Browser for any page on the Internet.
-
Way backpac (Tool): This is a tool that allows you to download the entire Wayback Machine archive for a given web page.
-
WebCite: Only archive history is avaiable.
-
oldweb.today: Retrieve archived web pages from the different public internet archives. You can also display archived websites using different web browsers.
Website monitoring services

Alert services
-
Update Scanner:A Firefox extension that Monitors web pages for updates.
RSS Tools And Services
Websites mirroring tools
-
HTTrack: Copy website for offline view.
-
GNU Wget: Retrieve files using HTTP, HTTPS, FTP and FTPS internet protocols.
-
BlackWidow: Download complete site or part of it and can download any kind of files- including YouTube videos embedded within it.
Link extractor
-
Link Gopher: This is a Firefox add-on that extracts all links from web pages, including the embedded one and display them in a new web page.
Check target website backlinks
-
To see all linked websites to a specific domain name, type the following in Google: site:* darknessgate.com (There should be a space between the asterisk and the domain name).
Identify technologies used
-
Built with: Give detailed technical information about the technology used to build target website.
-
dnslytics: To Find domains sharing the same Google Analytics ID.
IT devices Default Credentials
Vulnerabilities Database
Web Scraping Tools
-
Common Crawl: maintain an open repository of web crawl data that can be accessed and analyzed by anyone.
-
theHarvester: This is a tool for gathering subdomain names, e-mail addresses, virtual hosts, open ports/ banners, and employee names from different public sources like: Google, Bing, LinkedIn, Twitter, Yahoo, pgp and more.
-
Web data extractor (Commercial Application): Collect various data types including URLs, phone and fax numbers, email addresses, as well as meta tag information and body text.
-
80legs: (Commercial) Web Scraping Tools and Cloud-Based Web Crawling.
-
agenty: Cloud-based agents for data scraping, text extraction, ocr, categorization, change detection, sentiment analysis and more…
-
Anthracite: is a collection of Web mining power tools combined in an easy-to-use graphical environment that lets users quickly and seamlessly extract data from Internet sources, modify it to suit their needs, and export it to templates or databases, e.g. for RSS feeds.
-
apify: is a web scraping and automation platform for developers.
-
artoo.js: is a piece of JavaScript code meant to be run in your browser’s console to provide you with some scraping utilities.
-
scrapy:An open source and collaborative framework for extracting the data you need from websites.
Website certification search
Statistics & analytics Tools
Website Reputation Checker
WHOIS Lookup
Subdomain Discovery
-
Using Google search operator:Type site:target.com -inurl:www and Google will show all related subdomain names of the target. Example:site:yahoo.com -inurl:www ( Detailed instructions )
-
Amass: In-depth subdomain enumeration written in Go.
-
SecurityTrails: Sub-domain discovery and different online footprinting tests (associated domains, IPs, and SSL)
IP address tracking

IP Geolocation information
Information about IP (Internet Protocol)
BGP (Border Gateway Protocol)
-
BGP Stream: Show Global map of alerts about hijacks, leaks, and outages in the Border Gateway Protocol.
Blacklist IP addresses
 Online Maps
Online Maps
General Geospatial Research Tools
-
Digital Globe: Easy to use global map imagery tool with advanced search filters.
-
Bing Maps: Alternative to Google Map.
-
Yandex Maps: A Russian alternative to Google.
-
Baidu Maps: A Chinas alternative to Google.
-
Daum: Koran Map.
-
N2yo: Live streaming from different satellites. It also gives information about the tracked satellites and their coverage area.
-
Wigle: Wi-Fi networks mapping around the globe. It shows the Wi-Fi network name along with the access point MAC (Hardware) address, in addition to the possible location where free Wi-Fi is might be available.
-
BB Bike: Compare between two maps, for example, compare the same location map for Bing and Google map to see the difference in target location.
-
Newspaper map: List all newspapers around the globe on a map, you can filter according to location and newspaper language.
-
USGS: Search world map using different search criteria like address, place name or location coordinates. Map version is newer than Google maps.
-
Google Street View: View a specific location -must be existed within Google street view database- as if you are there.
-
Google maps Street View player: Show street view -where available- between two points on the map.
-
RouteView: Another Google map street viewer.
-
Open Street Cam: View open street cameras in a specific location -where available.
-
Zoom Earth: View international cloud imagery -updated each day- from NASA satellites.
-
Terrapattern: This is a visual search tool for satellite imagery, it allows you to search wide geographical area for specific visual effect. Currently, the search works in the following cities: New York, San Francisco, Pittsburgh, Berlin, Miami and Austin.
-
dominoc925: Show Military Grid Reference System (MGRS) Coordinates.
-
Mapillary: View street level imagery uploaded by people around the world. It gives a 3D view of many places (its database currently have 259,200,042), very useful to discover/investigate a specific location while you are not there.
-
Address Lookup: Find the address of any place on Google Maps.
-
Inspire Geoportal: Give access to European spatial data.
-
Hiking and Biking map: A map for hiking and biking.
-
Viamichelin: Show tourist, restaurants, hotels, traffic and weather on world map.
-
CORONA Project: List more than 800,000 images collected by the CORONA spy satellite launched by the United Sates and was in operation between 1960-1972.
-
Ani Maps: Create maps with interactive animations.
-
Trip Geo: Create a direction map using Google Street View data.
-
GeoGig: Open source tool which import raw geospatial data (currently from Shapefiles, PostGIS or SpatiaLite) into a repository to track any change to the data.
-
GRASS GIS: This is an open source Geographic Information System (GIS) software used for managing and analyzing geospatial data, spatial modeling, and visualization.
-
Timescape: This is a map based storytelling platform.
-
Polymaps: A JavaScript library for making dynamic, interactive maps in modern web browsers and supports different visual presentations to place on.
-
Mapquest: Helps you to find places on a map (Like Hotels, restaurants, coffee, Grocery stores, pharmacy, airport and many more), you can also use this service to find the best route -shortest one and estimated time to arrive- when going from one place to another.
-
NGA GEOINT: National Geospatial-Intelligence Agency official repository of map related tools on GitHub.
-
Free Map Tools: Find the radius around a point on the map.
-
Maphub: Create interactive map by adding points, lines, polygons or labels in addition to customized background.
-
Crowdmap: This is an annotation tool that allows you to visualize information on a map and timeline.
-
Maperitive: This is a Windows software for drawing maps based on OpenStreetMap and GPS data.
-
Perry-Castañeda Library Map Collection: List online maps of current interest around the world in addition to different map -including historical maps- of different locations around the world.
-
Roundshot: View live cameras from selected regions around the world.
-
Universal Postal Union: Find zipcodes of all countries.
Commercial Satellites
Global Date/Time
-
Wolframe Alpha: Enter a specific city/town or any location and the site will retrieve important information about it, like: Population, current local time, current weather, nearby cities, nearby airports, geographic properties and many more.
-
SunCalc: Shows sun movement during the course of the day for any given location on the map.
Location Based Social Media
Youtube
-
Geo Search Tool: This is a Geolocation search tool for YouTube geotagged videos. You can search for videos at a given address and in a given time-frame.
Facebook
-
Facebook Live: Go to Facebook live to see where there are live videos currently broadcasting. Live videos appear on a global map; a user can click over any live video -represented as a blue dot- to view/save it.
Twitter Geo-Location
-
Tweet Mapper: This is a free service to list all Geo-tagged tweets (All tweets posted while the “Location” feature is ON). All you need to do is to enter target Twitter handle then press ENTER. A map will appear showing red markers.
-
One Million Tweet Map: View world latest one million tweets on a map.
-
Qtr Tweets: Allows you to find all tweets within a specific distance from the target location on map, you can also search for keywords and filter the results according to a predefined criterion like: tweets with images and tweets with non-location data.
-
Tweet Map: Visualize all tweets on a global map, click over the points -which represent tweets- to read tweet content. You can also see top hash tags and tweets and search for them.
Other Geo-Location Social Media Tools
-
Strava Heat Map: This is a performance measurement sporting App for athletics; it works by monitoring athletic activities through the GPS sensor existed within their smartphone (supports Apple and Android) or any other supported devices. Strava heat map shows ‘heat’ made by aggregated, public activities over the last two years, this map is updated monthly.
Transport Tracking. Air Movements
-
Flight Aware: This company is considered the largest flight tracking data company in the world, it offers its flight tracking service free of charges for both private and commercial air traffic.
-
Flight Radar 24: Offer international real-time civilian flight tracking service, it tracks over 150000 flights per day and has the ability to track specific types of military jets (Like Russian and NATO jets) in some regions.
-
Air Cargo Tracker: Track air cargo for 190 airlines, you need to supply the Air cargo number to track the plane. The site also lists Airline code, Airline prefixes and Airport codes.
-
Radar Box 24: International airplane tracker.
Maritime Movements
-
Container Tracking: Track containers for 125 companies, you need to supply the container number only.
-
The international identification codes of container owners (BIC Codes)
Vehicles and Railway
-
ASM: Real time train tracking across the USA.
-
Train Time:Live map of London underground trains.
Package Tracking
-
After Ship: Track 447 couriers worldwide. Just enter the package number and it will automatically detect the courier company.
-
Tracking EX: Track 235 courier.
-
17 Track: Package tracking service.
-
Package trackr: Track global couriers and visualize the delivery path with Google Maps.
-
Boxoh: Package tracking service for USPS, UPS, FedEx, DHL/AirBorne.
Webcams
IP, MAC address data and service compilation for
OSINT computer intelligence.1. IP Data Retrieval
-
HostHunter - Detects and retrieves host names from a set of target IP addresses;
-
cyberhubarchive - Archive of data leaks, it contains IP addresses of Skype accounts;
-
spiderfoot.net - automatic search using a huge number of methods, but can be used in the cloud if you register;
-
iknowwhatyoudownload (http://iknowwhatyoudownload.com/) - shows what is being downloaded on the Internet;
-
recon.secapps.com - automatic search and link matching;
-
check.torproject.org - finds a list of all Tor output nodes in the last 16 hours that may have reached IP;
-
dnslytics.com - will find domains;
-
metrics.torproject.org (https://metrics.torproject.org/exonerator.html) - checks if IP address was used as a host for Tor traffic, date required;
2. Data search by MAC-address.
-
xinit.ru - shows Wi-Fi location;
-
alexell.ru - will also show the location.
-
wigle.net - finds Wi-Fi access point, its physical address and name;
3. Compilation of services for OSINT computer intelligence
List of services and utilities designed to analyze such data as IP, SSID, file metadata, DNS records and everything where the object of analysis is an element of IT structure, be it a site or IP address.-
Urlscan.io - checks to whom a TLS certificate was issued and which IP addresses are associated with the site.
-
PDFCandy - service allows to extract and modify PDF metadata.
-
wigle - can show SSID and BSSID of Wi-Fi access points on the map.
-
PublicWWW - the service searches for information on the source code of pages. Finds nicknames, links in the code, compares site icons, which allows you to search for twins; finds any similar links to identifiers or phrases, wallets, tokens, also allows you to find providers of advertising widgets, etc.
-
Metadata2Go - helps to find out all the metadata of a file.
-
HostHunter - searches for domain names using a set of IP addresses.
-
Knock Subdomain Scan - searches subdomains on the target domain and can generate an output file with the results.
-
Namechk - a site that will find all of a person's accounts in all social networks and
Before the OSINT AI BM service goes live, the first 1,000 users will get free access to the service for one year.
The service is scheduled to launch in September 2022.
-
 1
1








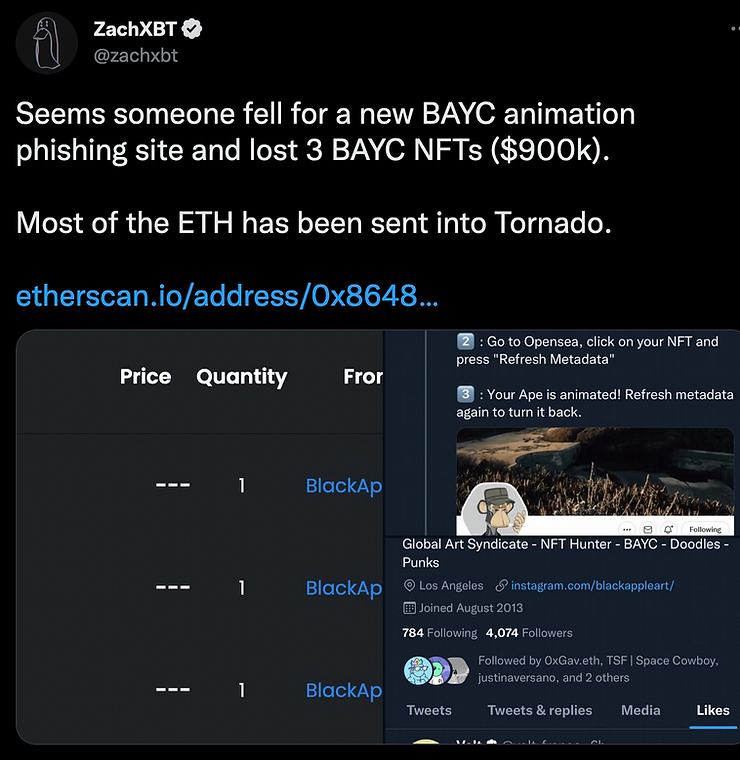

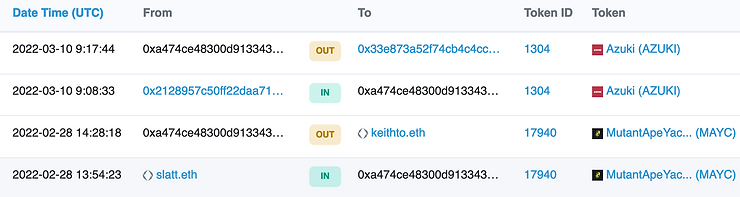
























































Основы информационной безопасности + контрольный список для проверки информационной безопасности организаций
in Инструкции
Posted
Основы информационной безопасности + контрольный список для проверки информационной безопасности организаций
Email.
Чаще всего именно электронная почта является главной точкой входа в тайны вашей компании и ее личного состава. Каждый официальный сайт компании содержит контактную информацию, включающую адрес электронной почты с доменом компании. Например, info@nameoforganization.com или hr@nameoforganization.com.
Это соответствует деловой этике, но в современном Интернете существует огромное количество инструментов (например, Google Dorks, phonebook.cz, hunter.io и др.), которые, используя домен, собирают другие адреса, которые организация, возможно, не хотела публиковать для широкой общественности. В результате можно обнаружить что-то вроде ciso@nameoforganization.com, andreypetrov@nameoforganization.com, SolyuVseSekretyKontory@nameoforganization.com.
Само наличие рабочего e-mail не только дает возможность установить прямой контакт с сотрудником, минуя отдел по связям с общественностью, но и позволяет коллегам использовать его не по назначению: регистрировать аккаунты в социальных сетях, заказывать доставку и так далее, и так далее, и так далее. Все это впоследствии скрывается. По таким электронным адресам можно найти много интересной личной информации, которая пригодится хакерам и кибершантажистам.
Фотографии сотрудников на сайте компании.
Да, фотографии на сайте компании могут помочь найти аккаунты ваших сотрудников в социальных сетях. В большинстве случаев эта информация не имеет коммерческой ценности, но это отличная возможность собрать сведения о личной жизни сотрудника, что может вылиться в настолько хорошо построенную социально-инженерную кампанию, что злоумышленник даже не заметит подвоха.
Кстати, существует достаточно много инструментов для поиска аккаунтов в социальных сетях по лицу. Например, FindClone, SearchForFace и даже просто google.pictures.
Публичная активность.
В действительности фотографии и публичная активность не являются столь критичными уязвимостями, как персональные данные, которые можно получить из адресов электронной почты. Исключить публичную активность компании - значит отсечь 80% маркетинга. Некоторые вещи стоит предавать огласке, а некоторые - нет.
Примером социально-инженерной атаки может служить такой текст, как: "Добрый день, я видел Вас на конференции "Легенды SOC - 2023". Нам очень понравилась ваша презентация. Мы хотели бы предложить Вам сотрудничество. Условия и подробное предложение находятся во вложении". Согласитесь, заманчиво! Особенно если ваша компания немного недоплачивает сисадмину, и он находится в поисках более выгодного предложения. Велика вероятность, что даже опытный ИТ-специалист сначала откроет вложение и только потом задумается.
Файлы на сайте компании.
Вам может казаться, что вы спрятали все ненужные файлы, но поисковые роботы Google все тщательно проиндексировали. Проверить это очень просто. Например, ваш сайт находится по адресу: rogaikopyta.site. Набираем в строке поиска google: filetype: (здесь без пробела формат файла -- pdf, doc, docx, xls, txt) site:rogaikopyta.site. Далее проверяем, чтобы ничего лишнего вдруг не оказалось в открытом доступе.
Есть ряд документов, которые юридическое лицо не может не публиковать, но то, что не входит в этот список, лучше почистить, ведь лишняя информация о ваших сотрудниках, контрагентах, финансовых активах - все это отличная пища для потенциальной атаки.
Хочется также обратить внимание на то, какие сотрудники представляют наибольшую угрозу для информационной безопасности компаний.
Большинство исследований в области информационной безопасности показывают, что самым слабым звеном в мерах безопасности являются сотрудники, поскольку именно они имеют полный доступ ко всем ресурсам и документам организаций.
Новый сотрудник ИТ-службы.
Новый сотрудник ИТ-службы может по неосторожности нанести огромный ущерб безопасности компании. Сегодня хакеры используют все более изощренные методы проникновения во внутренние ресурсы компаний, такие как социальная инженерия. Вновь принятый на работу ИТ-сотрудник не знаком с протоколами и процессами, обеспечивающими безопасную передачу файлов по сети, и поэтому является чрезвычайно привлекательной мишенью для злоумышленников, желающих получить полный доступ к корпоративной информации.
Системный администратор.
Во многих компаниях основными вопросами информационной безопасности занимаются системные администраторы. Сисадмин занимается не только техническими аспектами, но и несет огромную ответственность за материальные и нематериальные активы и репутацию организации. Кроме того, он знает о компании практически все, имеет доступ ко всем конфиденциальным данным, поэтому при определенных обстоятельствах может подвергнуться давлению со стороны киберпреступников.
Высшее руководство.
Как ни странно, генеральный директор компании на самом деле часто представляет собой огромную угрозу для ее информационной безопасности. По данным Ponemon Institute, более половины утечек, в которых участвуют сотрудники, происходят по вине высшего руководства. Такие потери являются наглядным доказательством того, что хакеры рассматривают в качестве своих целей не только менеджеров среднего звена, но и топ-менеджеров. Помощники руководителей также являются носителями очень ценной корпоративной информации. Они имеют доступ ко всем учетным данным, паролям, финансовым отчетам и внутренней документации. Именно это делает их особенно привлекательным объектом для взлома.
Консультант по безопасности.
Если вашей организации требуется сложная, многоступенчатая система безопасности, будьте готовы к сотрудничеству с различными поставщиками услуг из этой области. Однако помните, что внешний консультант по безопасности, привлеченный для определения текущего уровня безопасности и постановки задач в области ИБ, имеет полный доступ ко всем внутренним ресурсам компании и конфиденциальным данным, о чем хакеры прекрасно осведомлены.
Внешний поставщик
Крупные компании часто используют сразу несколько внешних поставщиков. Ежедневные хакерские атаки подтверждают, что после получения поставщиками доступа к внутренним системам и сетям компании эти системы и сети становятся особенно уязвимыми для киберугроз. Чтобы обезопасить себя, компании должны предоставлять поставщикам ограниченный и контролируемый доступ.
Уволенный сотрудник
Роковой ошибкой многих компаний является закрытие доступа к внутренним ресурсам и сетям для бывших сотрудников. Совершая эту ошибку, организации становятся еще более уязвимыми для кибератак. Единственным верным решением является немедленное удаление всех учетных записей сотрудников, которые уже не работают в компании. Более того, бывшие сотрудники могут легко унести с собой базы данных потенциальных и текущих клиентов и другую конфиденциальную информацию и разместить ее в свободном доступе в Интернете.
Временный работник
Временная занятость - очень распространенное явление, особенно в сфере обслуживания и продаж. Не является исключением и сфера информационных технологий, где очень часто требуются сотрудники на временной основе для решения тех или иных задач. Таким сотрудникам предоставляется доступ к различным корпоративным порталам и системам, где хранится наиболее важная информация и данные компании. Кроме того, временным сотрудникам предоставляются в пользование корпоративные ноутбуки, планшеты и смартфоны. Именно поэтому таких сотрудников следует считать полноправными членами организации и защищать от угроз информационной безопасности.
что речь пойдет не о технической стороне деятельности компаний, а о социальной инженерии, направленной на уязвимые места ваших сотрудников.
Помните, что именно сотрудники и их халатное отношение к мерам безопасности представляют собой огромную угрозу для ИТ-безопасности компании.
ДОПОЛНИТЕЛЬНАЯ ИНФОРМАЦИЯ, КОТОРАЯ МОЖЕТ ВАМ ПОМОЧЬ.
✅ ЧЕК-ЛИСТ ПРОВЕРКИ ОРГАНИЗАЦИЙ.
✅ 600 инструментов для osint и исследований.
✅ Инструменты для osint в blockchain.
✅ Маркетплейс для криптопроектов, все опции в одном месте.
✅ Инструменты для обеспечения безопасности смарт-контрактов.
✅ Новости osint, реальные расследования и полезная информация.